Malware, phishing, and DDoS attacks are just the tip of the iceberg when it comes to digital threats facing modern businesses. This guide breaks down these risks and explains how to protect your business from them. Whether it’s using strong passwords, monitoring your network for suspicious activity, or educating your employees, taking these steps will […]

From malware to phishing: Protecting your business from today’s cyber menaces

A 5-point security checklist for a hybrid workforce
Remote and hybrid work environments are great for reducing overhead and making your workforce happy, but this also means that employees will connect to your network from home offices, co-working spaces, and even public Wi-Fi networks. Each of these environments introduces new risks that can compromise sensitive company data if not properly managed.

Essential mobile security practices every business must implement
Discover essential best practices for effectively securing your mobile devices, from using strong passwords to using virtual private networks (VPNs) and keeping apps up to date. These simple steps can prevent costly data breaches and keep your company’s sensitive information safe from cybercriminals.

Why a SOC is your best defense against advanced threats
Cybersecurity threats continue to evolve, becoming more sophisticated, targeted, and difficult to detect. As a result, relying on basic tools or periodic security checks is no longer enough, not even for small to medium-sized businesses. A security operations center (SOC) offers a proactive, always-on approach to monitoring, detecting, and responding to threats, and fortunately, it’s […]

Office devices are becoming tools for scams: What you need to know
Cybercriminals are now using innocuous office devices such as printers and scanners to launch phishing attacks without needing to hack into your email account. Learn how to spot and stop this new trick to keep your workplace safe from phishing scams.

Why get a professional IT risk assessment?
Every week, another headline announces a costly data breach, leaving business leaders to wonder: What vulnerabilities are hiding in our network? And it’s a completely valid concern. The greatest risk often comes from the threats you don’t even know exist.
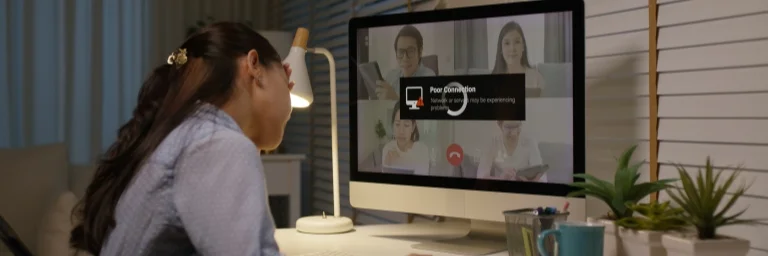
What happens to your VoIP system when the internet goes down?
You’re exploring the advanced features and significant cost savings of Voice over Internet Protocol (VoIP), but one critical question is holding you back: “If my entire phone system runs on the internet, what happens when that connection fails? Do we just go dark?” It’s a completely valid question that every smart business leader considers — […]

AI is great, but it creates a security blind spot
You’re focused on leveraging the latest technology for growth and innovation, but there’s a hidden risk that comes with it. The software, automated systems, and AI tools that power your business each have their own non-human identity (NHI). Managing these digital identities was a significant challenge even before the AI boom, but now, with intelligent […]

Think you can spot a phishing email? This new trick is harder to catch
Many people are getting better at spotting phishing attacks from outside sources. But what if the attack appears to come from within your own company? A recently discovered vulnerability in Microsoft 365 is being used to bypass traditional security, making it easier than ever for hackers to send you convincing fake emails that slip past […]

